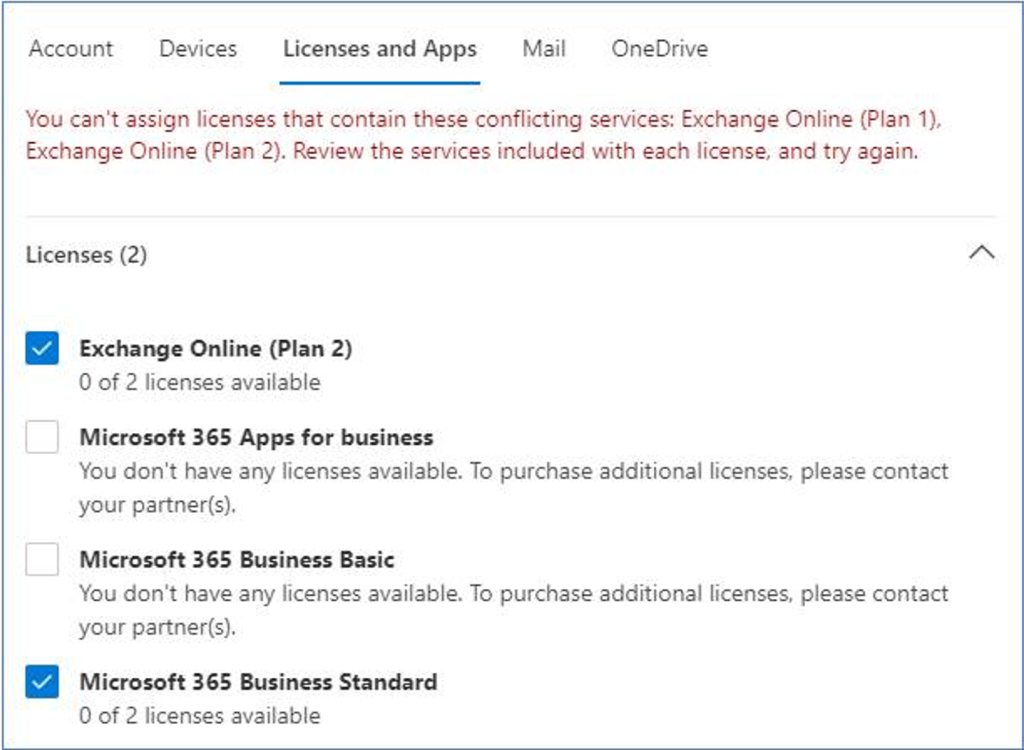
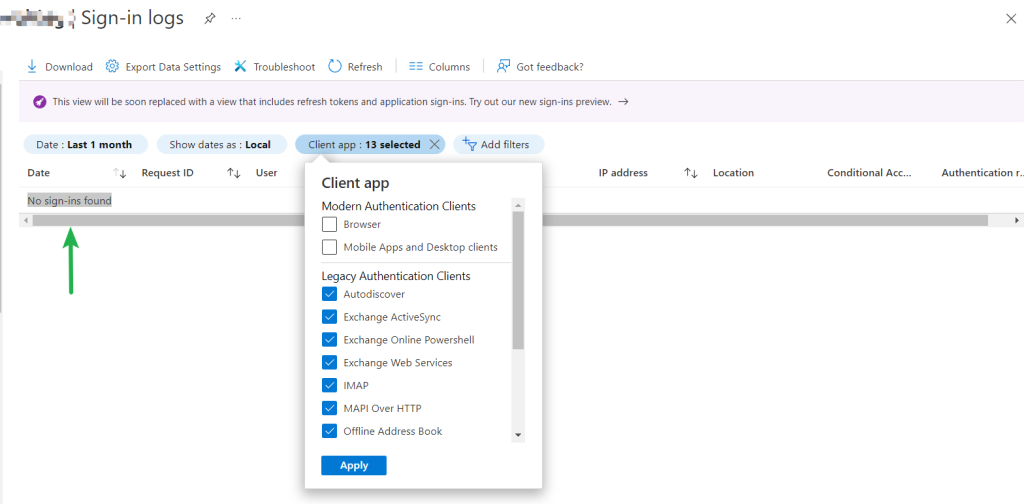
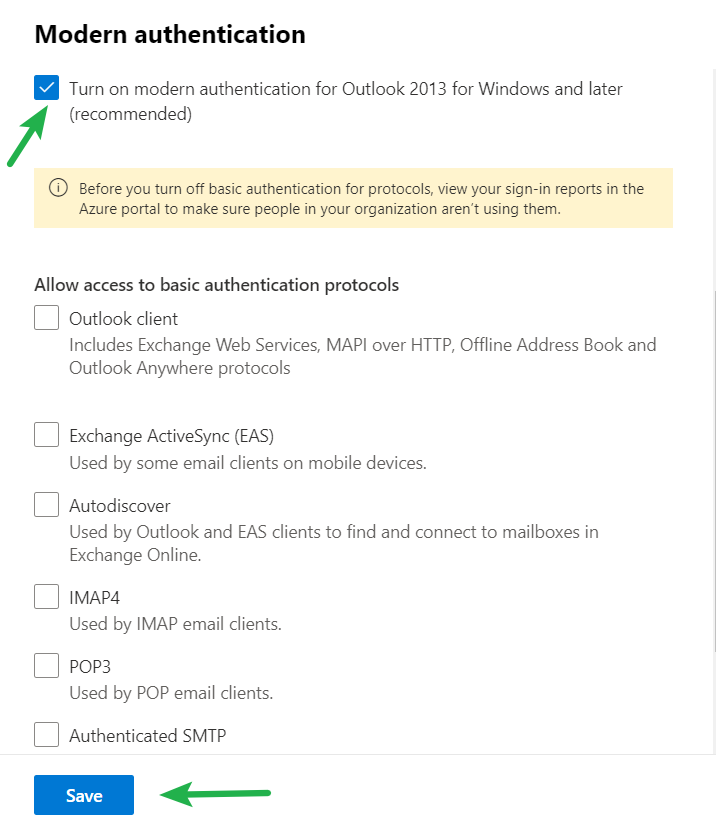
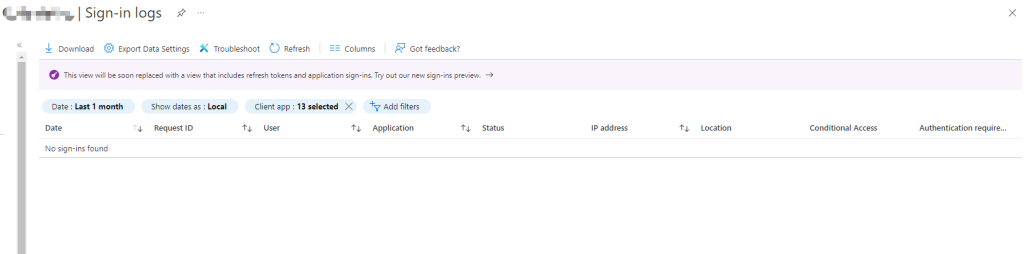
Yesterday was Groundhog Day and in honor of the great movie with the same name today’s #MicrosoftQuickFix is once again (get the reference now 😉) that Exchange Server 2013 is reaching end of support in 67 days from today on April 11, 2023!
After April 11, 2023, #Microsoft will no longer provide technical support for problems that may occur, bug fixes for newly discovered issues, security fixes for vulnerabilities that are discovered, and time zone updates.
Now look this doesn’t mean that because the Exchange Server software is out-of-date and no longer supported that it is going to stop working. Email will still flow, databases will still store data, mailboxes will still be accessible, but nefarious hackers will breathe a sigh of relief as the code now remains stagnant and despite “network magic” mitigation attempts all it takes is one zero-day venerability making its way in…
So your options are to Upgrade to Exchange Server 2019 – See the following page on Microsoft Docs for to Exchange Server 2019 system requirements, Exchange 2019 Requirements, Exchange 2019 Memory Requirements, Exchange 2019 Client Compatibility to begin.
Note: It is a supported coexistence scenario for Exchange 2019 and Exchange 2013 provided all your Exchange 2013 servers in your organization are patched to Exchange Server Cumulative Update 21 or higher.
and/or
Migrate to Exchange Online – See Decide on a migration path in Exchange Online on Microsoft Docs – Anyone still need a business case for migrating to #ExchangeOnline ?
In either case we recommend seeking assistance and using the Exchange Deployment Assistant which is a web-based tool that asks you about your current Exchange environment and generates a custom step-by-step checklist that will help you.
For more information about Exchange Server see:
- Exchange 2013 end of support roadmap
- Exchange Server build numbers and release dates
- Exchange Server supportability matrix
- Upgrade Exchange to the latest Cumulative Update
#Microsoft #Microsoft365 #MicrosoftExchange #ExchangeOnline #MicrosoftCloudSecurity #MicrosoftCloudQuickFix